Understanding Cryptography: Definition, Types, and Techniques Explained
Cryptography is an essential component of modern information security, playing a vital role in protecting data from unauthorized access and ensuring secure communication. As technology evolves, the methods and techniques of cryptography, such as curve cryptography, also adapt to meet new challenges. This article aims to provide a comprehensive understanding of cryptography, its definitions, types, techniques, and the challenges it faces in today’s digital landscape.
What is the Definition of Cryptography?
Cryptography is the practice and study of techniques for securing communication and information from adversaries. It involves the transformation of data into a format that is unreadable to anyone who does not possess the appropriate key, thereby protecting data from unauthorized access. This process is crucial for maintaining the confidentiality, integrity, and authenticity of information. Cryptography is used in various applications, including securing online transactions, protecting sensitive data, and ensuring the privacy of communications.
How does Cryptography Protect Data?
The primary purpose of cryptography is to protect data from unauthorized access and breaches. By utilizing cryptographic algorithms, data can be encrypted, rendering it unreadable without the corresponding decryption key. This process ensures that even if data is intercepted, it cannot be accessed or manipulated by unauthorized individuals. Additionally, cryptography helps in maintaining data integrity by using hash functions that create unique hash values for data, allowing for verification of its authenticity and enhancing overall data security. The use of digital signatures further enhances this protection by confirming the identity of the sender and ensuring that the data has not been altered during transmission.

What are the Key Concepts in Cryptography?
Key concepts in cryptography include algorithms, keys, and protocols. Cryptographic algorithms are mathematical formulas that govern the process of encryption and decryption, defining how data is transformed into an unreadable format and back again. Keys are critical components of these algorithms; they are the parameters that dictate the specific transformations applied to the data. The strength of a cryptographic system often relies on the length and complexity of its keys. Additionally, protocols are sets of rules that determine how cryptographic methods, including elliptic curve cryptography, are applied in practice, ensuring secure communication and data exchange.

What Role do Algorithms Play in Cryptography?
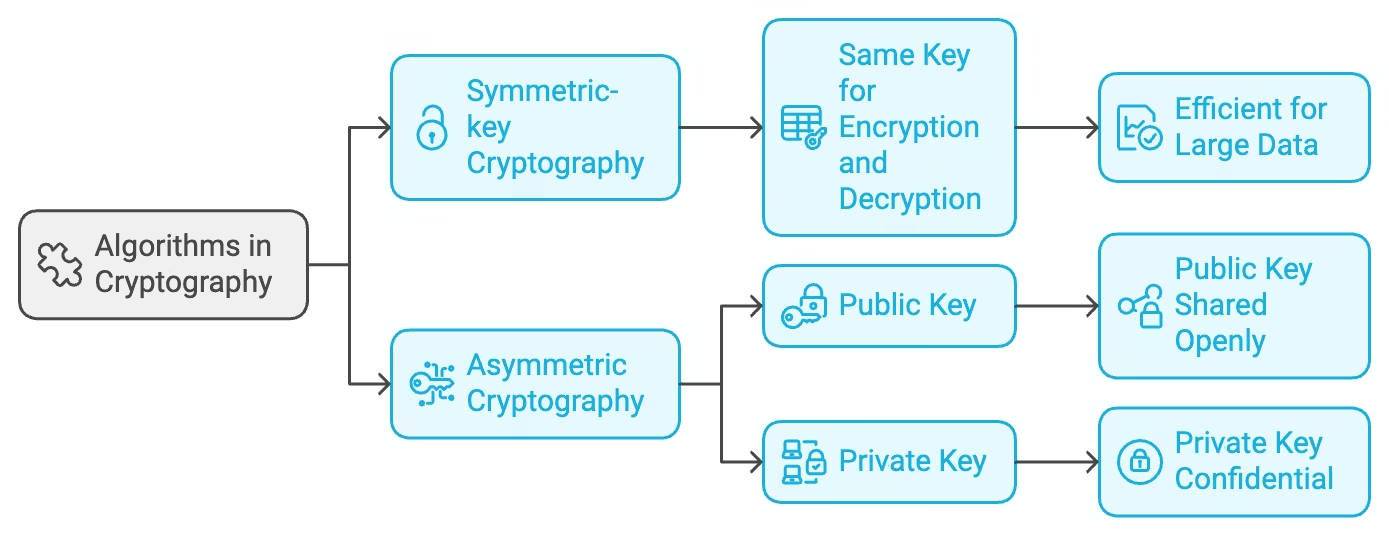
Algorithms are at the heart of all cryptographic processes, determining how data is encrypted and decrypted. There are various types of cryptographic algorithms, each designed to address different security needs. For example, symmetric-key cryptography uses the same key for both encryption and decryption, making it efficient for large amounts of data. In contrast, asymmetric cryptography employs a pair of keys, a public key and a private key, enhancing security by allowing the public key to be shared openly while the private key remains confidential. Understanding these algorithms is crucial for implementing effective cryptographic solutions.
What are the Different Types of Cryptography?
Cryptography can be broadly categorized into two main types: symmetric-key cryptography and asymmetric cryptography. Each type has distinct characteristics and applications, making it essential to understand their differences and use cases.
What is Symmetric-key Cryptography?
Symmetric-key cryptography, also known as secret key cryptography, involves the use of a single key for both the encryption and decryption processes. This type of cryptography is efficient and fast, making it suitable for encrypting large volumes of data, particularly when using optimized hash algorithms. However, the challenge lies in securely sharing the encryption key between the sender and receiver. If the key is intercepted during transmission, the security of the entire cryptographic system is compromised. Common symmetric encryption algorithms include the Advanced Encryption Standard (AES) and the Data Encryption Standard (DES), which are widely adopted for secure data encryption.
What is Asymmetric Cryptography?
Asymmetric cryptography, or public-key cryptography, uses a pair of keys: a public key that can be shared with anyone and a private key that is kept secret by the owner. This method enhances security by allowing users to encrypt messages with the recipient’s public key, which can only be decrypted using the corresponding private key. The use of asymmetric key cryptography is particularly beneficial for secure communication over the internet, where securely sharing a single key may be impractical. It also enables digital signatures, which authenticate the sender’s identity and ensure the integrity of the message.
How do Public Key and Private Key Work?
In public-key cryptography, the public key is available to anyone and can be used to encrypt messages intended for a specific recipient, enhancing secure communication between the sender and receiver. Upon receiving the encrypted message, the recipient uses their private key to decrypt it. This two-key system ensures that even if the public key is known, only the owner of the private key can access the encrypted information, providing a robust security mechanism. This method also allows for secure key exchange and the creation of digital signatures, thereby playing a pivotal role in modern cryptographic practices.
What are the Main Types of Cryptographic Algorithms?
Cryptographic algorithms can be divided into several categories, each serving different purposes and employing various techniques to secure data. Understanding these algorithms is crucial for effectively implementing cryptographic solutions.
What is a Hash Function in Cryptography?
A hash function is a fundamental concept in cryptography that takes input data and produces a fixed-size string of characters, which is typically a hash value. This value serves as a unique representation of the input data, enabling verification of data integrity. Cryptographic hash functions, such as SHA-256, are designed to be collision-resistant, meaning it is computationally infeasible to find two different inputs that produce the same hash value. Hash functions are widely used in various applications, including digital signatures and password storage, where secure verification of data is essential.

How do Encryption Algorithms Differ?
Encryption algorithms can differ significantly in terms of their structure, key length, and speed. Symmetric encryption algorithms, such as AES, use the same key for both encryption and decryption, while asymmetric algorithms, like RSA, utilize two different keys. The choice of encryption algorithm depends on the specific requirements of the application, including the desired level of security, performance, and ease of implementation. Understanding these differences is essential for selecting the appropriate algorithm to protect sensitive data.
What is the Advanced Encryption Standard (AES)?
The Advanced Encryption Standard (AES) is one of the most widely used symmetric encryption algorithms in the world. Adopted by the U.S. government, AES operates on fixed block sizes and supports key lengths of 128, 192, or 256 bits. Its strength and efficiency make it suitable for a broad range of applications, from securing data at rest to encrypting information during transmission. AES’s design ensures that it is resistant to most known attacks, making it a reliable choice for protecting sensitive information.
What are the Techniques Used in Modern Cryptography?
Modern cryptography employs a variety of techniques to ensure the security of data and communication. These techniques, including hash algorithms, are continually evolving to address new security challenges and technological advancements.
How is Digital Signature Used for Secure Communication?
Digital signatures are cryptographic techniques used to verify the authenticity and integrity of a message. When a sender encrypts a hash value of the message with their private key, it creates a digital signature that can be sent along with the message. Upon receipt, the recipient can decrypt the signature using the sender’s public key and compare the hash value with the hash of the received message. If the two hash values match, it confirms that the message has not been altered and verifies the sender’s identity, thereby ensuring secure communication.
What are Cryptographic Keys and Their Importance?
Cryptographic keys are vital for the encryption and decryption processes, serving as the secret parameters that determine how data is transformed. The strength of a cryptographic system heavily relies on the security and complexity of these asymmetric encryption keys. A longer and more complex key typically results in a more secure encryption. Key management is a critical aspect of cryptography, involving the generation, distribution, and storage of keys to prevent unauthorized access. Effective key management practices are essential for maintaining the overall security of cryptographic systems.
How is Post-Quantum Cryptography Different?
Post-quantum cryptography refers to cryptographic algorithms designed to be secure against the potential threats posed by quantum computing. Quantum computers have the capability to solve certain mathematical problems much faster than classical computers, leading to concerns about the vulnerability of existing cryptographic schemes, particularly those based on integer factorization and discrete logarithms, such as RSA and ECC. Post-quantum cryptography aims to develop new algorithms that can withstand these quantum attacks, ensuring the continued security of encrypted data in the future through advanced mathematics.

What are the Concerns and Challenges in Cryptography?
Despite its critical role in information security, cryptography faces several concerns and challenges that must be addressed to maintain effective data protection through mathematics and computer science principles.
What are the Risks Associated with Cryptographic Systems?
The risks associated with cryptographic systems include vulnerabilities in algorithms, poor key management practices, and implementation flaws. An outdated or weak cryptographic algorithm can expose data to potential breaches. Furthermore, if cryptographic keys are not managed securely, they may be compromised, leading to unauthorized access to sensitive information and undermining data security. Regular updates and adherence to cryptography standards are essential to mitigate these risks and ensure the ongoing effectiveness of cryptographic systems.
How Do Cryptography Techniques Evolve with Technology?
As technology advances, so do the techniques used in cryptography. New threats emerge, and existing algorithms may become vulnerable due to advancements in computational power and techniques. Cryptography continually evolves to address these challenges, with researchers developing new algorithms and techniques that enhance security. For instance, the rise of quantum computing has spurred the development of post-quantum cryptography to prepare for potential threats to current cryptographic methods. Staying informed about these advancements is crucial for organizations to protect their data effectively.
What are the Implications of Cryptography on Cryptocurrency?
Cryptography plays a pivotal role in the functioning of cryptocurrencies, where it secures transactions and maintains the integrity of the blockchain. Public-key cryptography is used to generate wallet addresses and secure transactions, while hash functions ensure that transaction data cannot be altered without detection, providing an essential layer of data security. The reliance on cryptographic techniques in cryptocurrencies highlights the importance of robust security measures in this rapidly growing field. As cryptocurrencies continue to gain popularity, understanding the cryptographic principles underlying them is essential for users and investors alike.
Cryptography in Modern World
Cryptography has become a cornerstone in ensuring the secure information and communication techniques we rely on today. The history of cryptography can be traced back centuries, evolving to modern cryptography, which exists in various forms like symmetric key cryptography and quantum cryptography. Cryptography is based on the idea of using an algorithm to protect data through encryption. One of the most popular cryptography algorithms is the Secure Hash Algorithm, particularly Secure Hash Algorithm 1 (SHA-1), which plays a significant role in Transport Layer Security (TLS). Key cryptography is crucial for protecting sensitive information, with cryptography ensuring a strong layer of security for digital communications. Applications of cryptography are vast, covering everything from securing financial transactions to safeguarding personal data. Cryptography concerns not only the encryption process but also cryptography and cryptanalysis, which involves studying methods to break these security systems. Quantum cryptography, a cutting-edge field, further advances how cryptography provides secure solutions. With various types of encryption protocols, cryptography remains essential in maintaining trust in digital ecosystems, and cryptography is closely tied to securing online interactions.
FAQ
Q: What is the definition of cryptography?
A: Cryptography is the practice and study of techniques for securing communication and data from adversaries. It involves the use of mathematical algorithms and protocols to encrypt and decrypt information, ensuring confidentiality, integrity, and authenticity.
Q: What are the two main types of cryptography?
A: The two main types of cryptography are symmetric-key cryptography and asymmetric cryptography. Symmetric-key cryptography uses a single key for both encryption and decryption, while asymmetric cryptography uses a pair of keys—a public key for encryption and a private key for decryption.
Q: Can you explain what a cryptographic algorithm is?
A: A cryptographic algorithm is a mathematical procedure used for encryption and decryption of data. It defines how the data is transformed to protect its confidentiality and integrity. Examples of cryptographic algorithms include the Advanced Encryption Standard (AES) and RSA.
Q: What is the role of a public key in public key cryptography?
A: In public key cryptography, the public key is used to encrypt data, whereas the corresponding private key is used to decrypt it. This allows secure communication without sharing a secret key, making it essential for tasks like digital signatures and secure online transactions.
Q: What is a hash function in the context of cryptography?
A: A hash function is a cryptographic algorithm that takes an input (or ‘message’) and produces a fixed-size string of bytes, which is typically a hash value. It is used to ensure data integrity, as any change in the input will result in a different hash value, making it easy to detect alterations.
Q: How does modern cryptography differ from historical cryptography?
A: Modern cryptography relies on complex mathematical algorithms and computational power to secure data, while historical cryptography often used simpler substitution and transposition techniques. Modern methods also address contemporary concerns such as secure communication over the internet and resistance to quantum computing threats.
Q: What are some common cryptography techniques used today?
A: Common cryptography techniques include symmetric encryption (like AES), asymmetric encryption (like RSA), hashing algorithms (like SHA-256), and digital signatures. These techniques are used to protect data, ensure secure communication, and verify the authenticity of information.
Q: What is post-quantum cryptography?
A: Post-quantum cryptography refers to cryptographic algorithms that are believed to be secure against the potential threats posed by quantum computing. As quantum computers become more powerful, traditional cryptographic systems may be vulnerable, making the development of post-quantum algorithms crucial for future information security.
Q: How can cryptography be used to protect data?
A: Cryptography can protect data by encrypting it, making it unreadable to unauthorized users. This ensures that even if data is intercepted, it cannot be understood without the appropriate cryptographic key. Additionally, techniques like hashing can verify data integrity and authenticity.
Q: What are the concerns surrounding cryptography?
A: Concerns surrounding cryptography include the potential for cryptographic keys to be compromised, the risks posed by advances in quantum computing, and the balance between security and usability. Additionally, there are legal and ethical implications regarding privacy and surveillance associated with the use of cryptography.



